The Sovereign Shield: How the Gulf Is Rewriting the Rules of Cyber Defense

What the Gulf is building isn’t reactive. It’s a refusal to repeat the world’s mistakes.
While others are still patching holes in the dam, the Middle East built upstream.
What began as a constraint—no legacy to inherit—became a rare advantage: systems that can see, correlate, and respond in real time.
This is what happens when resilience becomes a design principle, not a post-mortem.
What follows is a breakdown of how the Gulf is rewriting cyber defense, and what the rest of the world can learn from it.
The Security-First Manifesto
Breaking the Build-Then-Secure Paradox
Across the global cyber landscape, there's one region that has decisively flipped the script: the Middle East.
While the Gulf is making cybersecurity a fundamental principle of operating critical infrastructure, other regions continue to treat cybersecurity as a band-aide measure largely governed by ex post facto regulation.
- In the U.S., major reforms often followed high-profile breaches—Colonial Pipeline was not an exception, but a catalyst.
- Across the EU, privacy regulations advanced quickly, but real-time cyber defense has lagged behind.
- In Southeast Asia, digital growth is outpacing the security needed to sustain it.
The Gulf is breaking this pattern.
It isn’t retrofitting resilience. It’s designing it into the fabric of its infrastructure.
This isn't an evolution. It's a deliberate inversion.
From smart city infrastructure to national energy grids, security is being treated not as a feature, but as a foundational layer (Haciane & Abboud, 2025). By designing threat visibility, incident response, and contextual risk modeling alongside infrastructure, the region has reduced its attack surface and neutralized critical attack vectors.
In the span of just a few years, the Gulf’s security philosophy has matured into a sovereign architecture that doesn’t just detect threats—it anticipates and neutralizes them before deployment.
This isn’t just the result of better dashboards. It’s what happens when threat intelligence is fused with asset visibility, contextual risk modeling, and real-time telemetry from the start.
From OT-aware anomaly detection to AI-native correlation engines, the Gulf is deploying systems trained to spot deviations before they escalate—across energy grids, transportation networks, healthcare facilities, and so much more.
These aren’t isolated regulations—they form the backbone of a national cyber defense strategy that’s already producing measurable results.
The result?
The Gulf has achieved a tangible reduction in exposed risk and a dramatic acceleration in secure deployment timelines. This shift isn’t just architectural—it’s economic.
According to research by Security Compass (2023) and Practical DevSecOps (2023), organizations that adopt security-by-design practices experience up to 79% fewer exploitable vulnerabilities and six times lower remediation costs compared to reactive models.
This is where the region breaks from global convention.
The Gulf isn’t measuring checkbox compliance—it’s measuring operational command.
While most compliance frameworks focus on proving audit readiness or the presence of controls, the Gulf is focused on something else entirely: proving performance.
Security As Critical Utility
The National Resilience Framework
Cybersecurity in the Gulf isn't a department. It is infrastructure.
It's a national cyber defense strategy woven into every digital project.
Security in the Middle East is no longer relegated to IT departments. It's been elevated to a utility-class system, as essential to national continuity as water, power, or transport.
Regulatory mandates in the Gulf have redefined cybersecurity compliance as a matter of national interest. These aren’t just policy suggestions. They are sovereign imperatives.
In Saudi Arabia, the National Cybersecurity Authority (NCA) has issued frameworks such as the Essential Cybersecurity Controls (ECC) and the Critical Systems Cybersecurity Controls (CSCC)—mandating that cybersecurity be embedded at the architectural blueprint phase of digital infrastructure.
In the UAE, cybersecurity has become a national directive. The Personal Data Protection Law (PDPL) and the National Artificial Intelligence Strategy 2031 elevate cybersecurity to a core pillar of digital transformation, mandating secure-by-design practices across both data governance and AI operations.
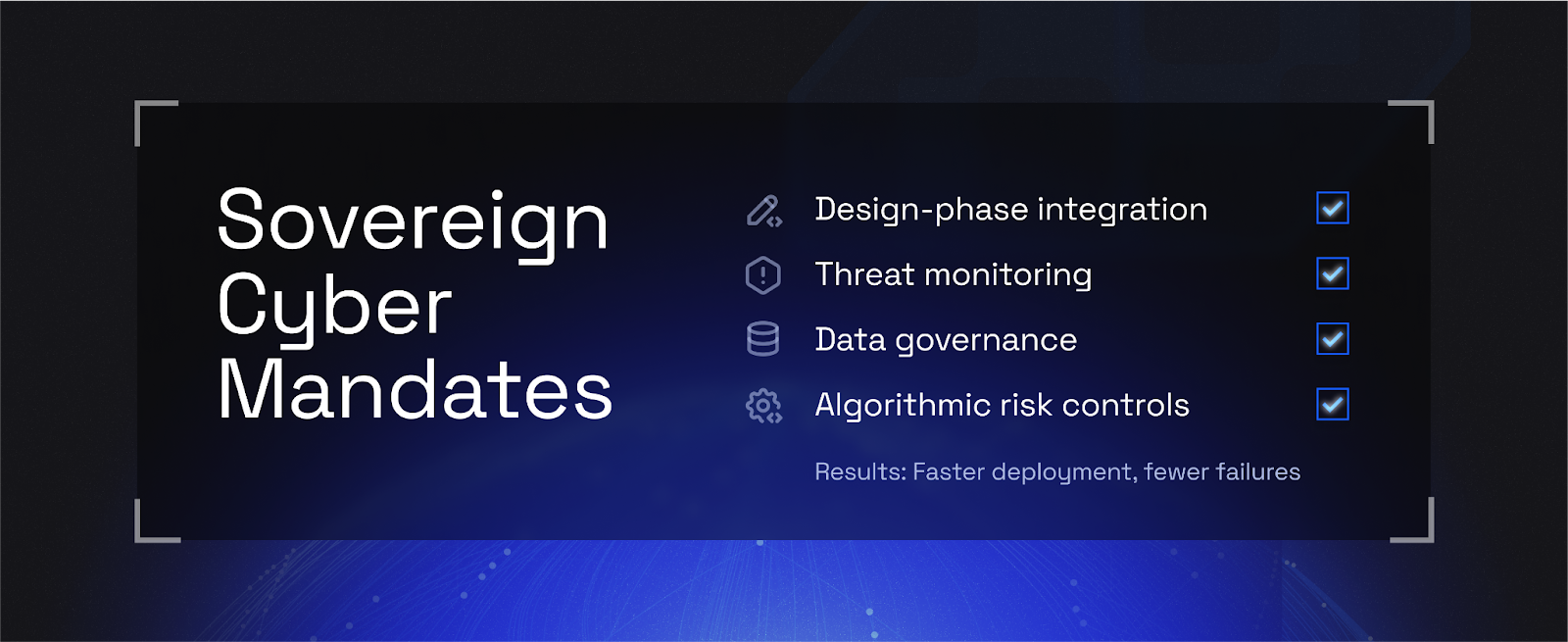
Together, these frameworks demand:
- Integration of cybersecurity controls into infrastructure from the design phase
- Mandatory access controls, threat monitoring, and incident response protocols
- Explicit consent, encryption, and breach reporting for data systems
- Governance mechanisms for algorithmic risk and secure data sharing
And the result?
- Faster deployment cycles
- Fewer last-mile compliance failures
- Infrastructure that launches with security already in place—not bolted on after
By embedding cybersecurity from day one, Gulf nations are accelerating launches—avoiding delays from retroactive patching, fractured telemetry, or last-minute compliance cycles.
Cybersecurity here isn’t a constraint. It’s a catalyst. And it’s redefining how nations measure digital competitiveness.
Zero-Legacy Advantage
Turning Historical Disadvantage Into Digital Sovereignty
The region's late entry into large-scale digital transformation has become its greatest architectural asset.
Unburdened by outdated legacy systems, Middle Eastern states are constructing cybersecurity ecosystems unified by design. Telemetry isn't stitched together post-deployment—it's orchestrated from inception, providing integrated visibility across operational technology (OT), information technology (IT), cloud technologies, and identity systems.
This approach obliterates one of the most common failure points in today’s cyber systems: silos.
In many legacy environments, threat intelligence flows vertically—from endpoint detection systems to SIEM dashboards—but remains disconnected from industrial control systems, building management platforms, or transport telemetry.
In the Gulf, threat telemetry moves horizontally across sectors, giving defenders a comprehensive, real-time view of the threat landscape (Claroty, 2025; Nozomi Networks, 2024)
The outcome is transformative: organizations aren't reacting to incidents—they're anticipating them. With proactive anomaly detection, cross-domain correlation, and adaptive defense postures, systems evolve with each attack vector they encounter.
This is digital sovereignty executed with precision: architecture that isn't just independently governed but operationally dominant; built without the friction of legacy compromise.
Exporting What Already Works
This isn’t a regional anomaly. It’s a working prototype.
What’s been built across Riyadh, Abu Dhabi, Doha, and Manama isn’t just relevant to the Gulf—it’s a model for any system that needs to move faster than its risk surface. These governments didn’t debate the shift from compliance to capability. They made it.
Smart finance platforms. Healthcare delivery systems. National digital infrastructure. All rest on a single architectural truth:
If you can’t see the threat, you can’t contain it.
The Gulf has proven that security-by-design isn’t theory. It scales. And the downstream effects aren’t marginal—they’re exponential.
The region's approach distills into four commandments:
● Begin with visibility: map all assets, inputs, and cross-domain dependencies before a single line of code is written.
● Build for correlation: eliminate siloed dashboards in favor of unified threat landscapes.
● Design for scale: architect systems that strengthen—not degrade—under increased load and complexity.
● Regulate for resilience: measure response capability, not control presence.
This isn’t compliance theater.
It's a system-level command, and the results are already live.
Executive Takeaways: Lessons That Travel
If you're still retrofitting security, you're already behind.
The Gulf isn’t experimenting. It’s executing. And the operational standard it has set is no longer emerging—it’s here.
Here’s what that looks like:
- Design security from blueprint, not from hindsight
- Unify telemetry—across sectors, not within silos
- Move from alerts to context to coordinated response
- Verify readiness, not control presence
- Stop treating security as a department. It’s now direction
This isn’t best practice. This is what modern cyber risk management looks like—engineered, enforced, and executed at scale. It’s the threshold.
Rilian’s Middle East Bet: Why We Doubled Down Early
Not an expansion. A force multiplier.
Our early commitment to the Gulf wasn’t about market capture—it was about mission alignment. The region had already architected a bold vision for cyber resilience. What it needed next was operational execution at scale.
That’s where we come in.
While others shipped tools, we embedded systems.
While others promised dashboards, we delivered telemetry—live, unified, sovereign-controlled.
Where others offered control libraries, we enabled decision frameworks.
We built alongside the region’s critical infrastructure—across energy, mobility, finance, and public-sector systems—bringing:
- Sovereign-native architecture, aligned with regional governance
- AI-native risk modeling, trained on infrastructure behaviors
- Cross-sector telemetry, stitched across OT, IT, CT, and cloud
- Operator-first interfaces, tuned for clarity, not complexity
- Autonomous execution, from blueprint to deployment
This wasn’t a retrofit. It was acceleration—purpose-built for a region that refuses to move slowly.
The Resilience Imperative
You don’t need more tools. You need more visibility.
The Gulf is proving that real resilience is built—not bought.
It starts with unified telemetry, contextual intelligence, and systems that respond faster than threats can evolve.
This isn’t theory. It’s already live.
If your infrastructure is growing faster than your defense model, you’re not building for scale. You’re building for breach.
Real resilience starts when visibility is non-negotiable.
Let’s assess your readiness - not just your tools.Get in touch with us here.
References
- Haciane, K., & Abboud, R. (2025, January 31). link
- Security Compass. (2023). The high costs of delaying a Security by Design program. link
- Practical DevSecOps. (2023). Maximizing DevSecOps ROI: 6 key benefits you can’t ignore. link
- National Cybersecurity Authority. (2018). Essential Cybersecurity Controls (ECC-1:2018). link
- National Cybersecurity Authority. (2019). Critical Systems Cybersecurity Controls (CSCC-1:2019). link
- Federal Decree-Law No. 45 of 2021 on the Protection of Personal Data. (2021). link
- UAE National Strategy for Artificial Intelligence 2031. (2021). Retrieved from link
- Claroty. (2025). link
- Nozomi Networks. (2024). Nozomi Networks Launches First SaaS Platform for OT and IoT Security in UAE. link







.jpeg)
